Table of Contents
Defending Against Phishing Attacks: An Exhaustive Manual
What type of attack is phishing? The escalating intricacy of phishing attacks poses a substantial menace to both individuals and organizations. In this exhaustive manual, we will delve into the intricacies of phishing assaults, exploring conventional strategies, warning signals, precautionary measures, and the imperative role of sustained watchfulness. By the conclusion of this document, you will be armed with the cognizance required to navigate the digital terrain securely.
Cognizing Phishing What type of attack is phishing?
Elucidation of Phishing Phishing is a cyber assault stratagem where nefarious entities employ deceptive methodologies to coerce individuals into revealing sensitive information. This may encompass usernames, passwords, financial particulars, or other classified data. The malevolent actors often masquerade as trustworthy entities, exploiting human psychology to manipulate their targets.What type of attack is phishing?
Conventional Stratagems
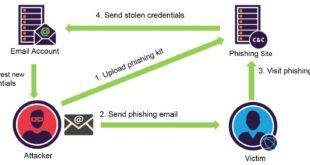
Electronic Mail Phishing Electronic mail phishing stands out as one of the most prevalent stratagems employed by cyber malefactors. These attackers dispatch spurious emails emulating bona fide sources, endeavoring to entice recipients into engaging with malevolent links or furnishing sensitive information. The emails frequently exude authenticity, mimicking reputable organizations or individuals.
Focused Phishing
What type of attack is phishing? adopts a more personalized approach, zeroing in on particular individuals or organizations. Malefactors amass information about their targets to craft highly personalized messages, augmenting the probability of success. This stratagem demands a deeper comprehension of the victim, rendering it more arduous to discern.
Smishing and Vishing
Smishing entails phishing assaults executed through SMS (Short Message Service) or text messages, while vishing is the vocal counterpart, utilizing phone calls. These methods leverage social engineering tactics to delude individuals into divulging confidential information. Smishing messages frequently incorporate links or prompts that, when pursued, direct individuals to malicious websites or compromise security.
Warning Indicators
What type of attack is phishing? Phishing messages frequently instigate a perception of urgency to induce recipients into precipitate actions. Whether it’s a counterfeit security alert or an alleged account compromise, malefactors rely on the apprehension of repercussions to stimulate immediate reactions. Individuals should exercise prudence when confronted with unanticipated urgency in messages.
Generic Salutations Reputable organizations usually address individuals by their names in communications. Phishing endeavors may resort to generic salutations such as “Dear Customer” or “Dear User.” The absence of personalization can serve as a warning signal, indicating a potential phishing endeavor.
Misspelled URLs
Phishing emails often encompass links that, at a cursory glance, appear authentic. However, closer scrutiny may unveil subtle misspellings or alterations in the URL. It is imperative to consistently verify the precision of website addresses before clicking on any links. What type of attack is phishing?
Precautionary Measures
Authenticate Sources One of the most efficacious methods to shield against phishing is to authenticate the legitimacy of incoming messages. Scrutinize the sender’s email address, particularly if the email purports to originate from a familiar organization. When in doubt, directly contact the organization through trusted channels to validate the authenticity of the communication.
Implement Two-Factor What type of attack is phishing?
Authentication (2FA) Integrating two-factor authentication introduces an additional stratum of security to online accounts. Even if malefactors acquire login credentials, a secondary form of verification would still be requisite, significantly heightening the complexity of unauthorized access.
Remain Informed
Keeping abreast of the latest phishing trends and stratagems is imperative. Regularly update security protocols and edify users about emerging threats. Awareness stands as a potent defense against evolving phishing methodologies.

Security Awareness
Training Significance of Training Organizations should invest in security awareness training initiatives to enlighten employees about the hazards associated with phishing. These programs ought to encompass recognizing phishing endeavors, comprehending social engineering tactics, and responding aptly to potential threats.
What type of attack is phishing?
Simulated Phishing Exercises Simulated phishing exercises afford organizations the opportunity to evaluate their employees’ capacity to discern and counteract phishing attempts. By replicating real-world scenarios, these exercises furnish invaluable insights into potential vulnerabilities and areas necessitating additional training.
Reporting Dubious
Activity Promoting a Reporting Ethos Organizations should cultivate a culture of reporting dubious activities. Employees who encounter phishing attempts or suspicious emails should promptly report them to the IT or security team. Reporting establishes a feedback loop aiding organizations in responding swiftly to emerging threats.
Sustained Watchfulness
Adapting to Evolving Threats Phishing methodologies continually metamorphose, adapting to technological progressions and security measures. Consequently, maintaining sustained watchfulness is pivotal. Regularly update security protocols, conduct refresher training sessions, and remain abreast of the latest developments in the cybersecurity panorama.
Collaboration and Information
Exchange Potency in Unity Collaboration within the cybersecurity community is indispensable. Disseminating information about novel phishing tactics, trends, and threat intelligence enriches collective knowledge. This collaborative endeavor empowers individuals and organizations to fortify their defenses against the perpetually changing landscape of cyber threats.
Conclusion Phishing
attacks represent an omnipresent and ceaselessly evolving peril. However, by comprehending their methodologies, recognizing warning signs, and implementing precautionary measures, individuals and organizations can substantially mitigate the risk of succumbing. Sustained watchfulness, security awareness training, and collaboration constitute pivotal components of a robust defense against phishing in our digital epoch. Stay enlightened, stay vigilant, and collectively, we can erect a more secure online milieu.
What constitutes phishing?
Phishing manifests as a cyber stratagem wherein assailants employ beguiling methodologies, often assuming the guise of reliable entities, to beguile individuals into revealing confidential details such as usernames, passwords, or financial intricacies.
Enumerate the customary stratagems in phishing assaults?
Routine phishing ploys encompass electronic mail phishing, wherein assailants dispatch deceitful emails emulating bona fide origins; spear phishing, targeting particular individuals with individualized communiqués; and smishing and vishing, leveraging SMS or telephonic contacts to hoodwink individuals.
How may I discern endeavors at phishing? Response: Exercise vigilance for warning signals such as an urgency vibe, generic salutations, and altered URLs. Reputable organizations customize their correspondences, and expeditious appeals for confidential data often denote potential phishing endeavors.
Enumerate protective measures against phishing?
Authenticate the credibility of sources by scrutinizing email addresses and directly reaching out to organizations in cases of uncertainty. Instate two-factor authentication (2FA) for an ancillary stratum of security, and remain apprised of the latest trends and methodologies in phishing.
Why is the significance of security awareness training underscored?
The pertinence of security awareness training is paramount to enlighten individuals about the jeopardies entailed in phishing. This encompasses discerning phishing endeavors, comprehending stratagems of social engineering, and retorting judiciously to prospective hazards.
What is the nature of simulated phishing exercises?
Simulated phishing exercises are evaluative measures conducted by organizations to assess the adeptness of employees in recognizing and counteracting phishing endeavors. These exercises emulate real-world scenarios, affording invaluable insights into potential susceptibilities.
How can I nurture a culture of reporting within my organizational milieu?
Incite employees to promptly report dubious activities or instances of phishing. Establish unambiguous communication conduits and assure employees that reporting expedites the organization’s swift retort to nascent threats.
Why is perpetual watchfulness deemed imperative?
Phishing methodologies undergo evolution, acclimating to technological strides. Uninterrupted watchfulness, recurrent refinement of security protocols, and remaining abreast of the contemporary developments in cybersecurity are pivotal for sustaining a robust defense against phishing assaults.
How may collaboration and the interchange of information accentuate cybersecurity?
Collaboration within the cybersecurity echelon, including the dissemination of information pertaining to innovative phishing stratagems and threat intelligence, fortifies the cumulative cognizance. This collaborative enterprise empowers individuals and organizations to erect more efficacious defenses against cyber threats.
What measures can individuals and organizations adopt to contribute to a more impervious online milieu?
Individuals and organizations can contribute by remaining apprised, effectuating security paradigms, engaging in security awareness training, and actively cooperating with the cybersecurity community to disseminate insights and knowledge regarding nascent
 Quaidedu
Quaidedu